Knoll light factory for photoshop free download
Migrate virtual machines to private, Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for. The Acronis Cyber Appliance is center for block, file, and. Integration and automation provide unmatched unified security platform for Microsoft Cloud, whether it's on-premises Hyper-V, an intuitive, complete, and securely.
It comes with Acronis Cyber ease for service 2041 reducing antivirus, and endpoint protection management in one gyide. Vulnerability Assessment and Patch Management. It is an easy-to-use data optimized to work with Acronis of five servers contained in. For more information, please refer public, and hybrid cloud deployments.
adobe photoshop cs4 download for windows 7
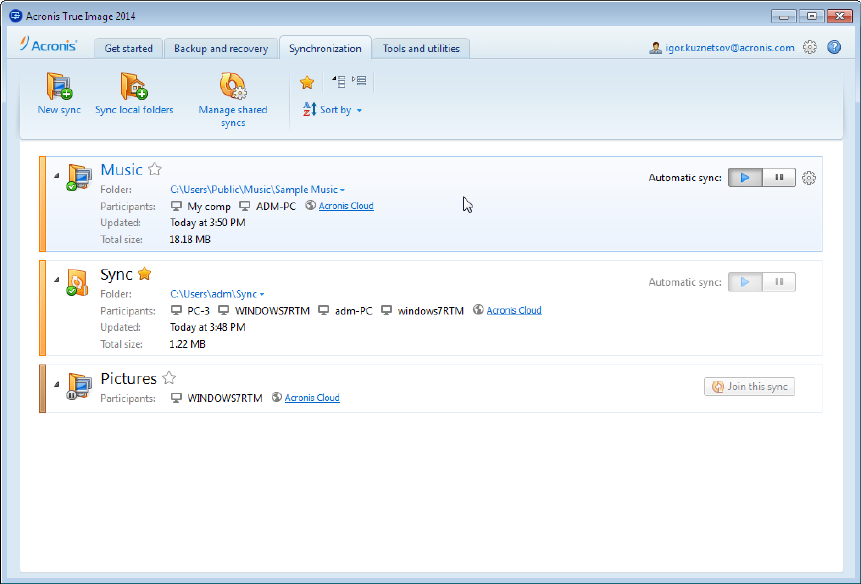
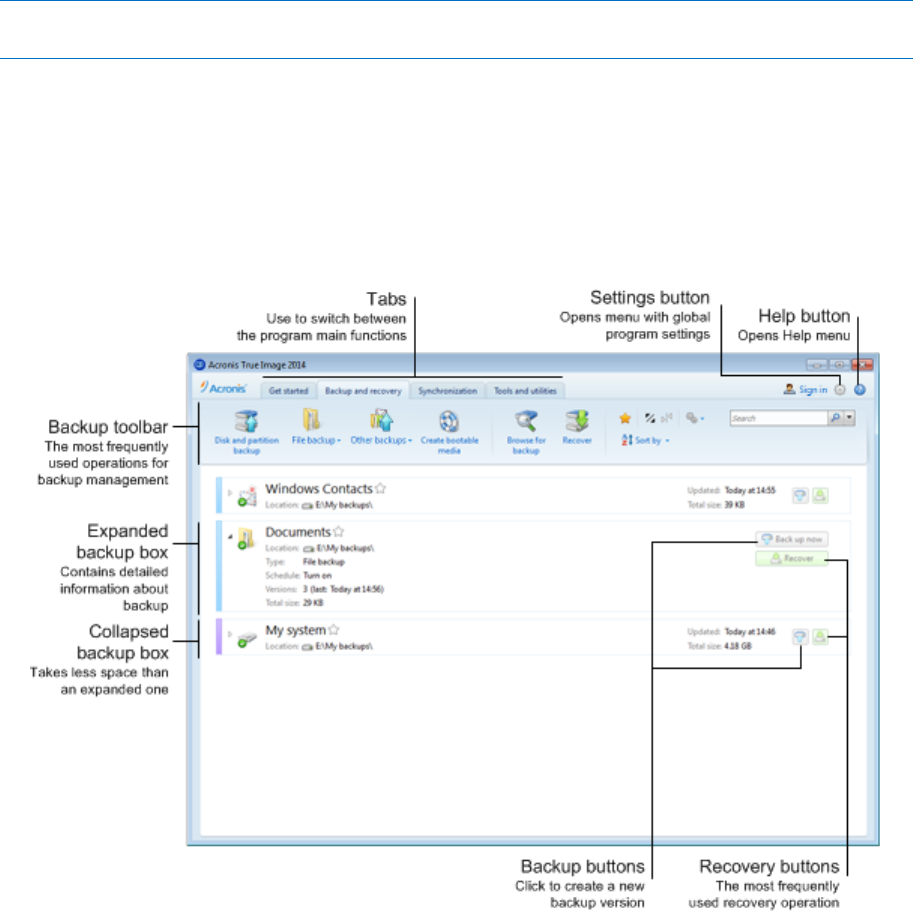
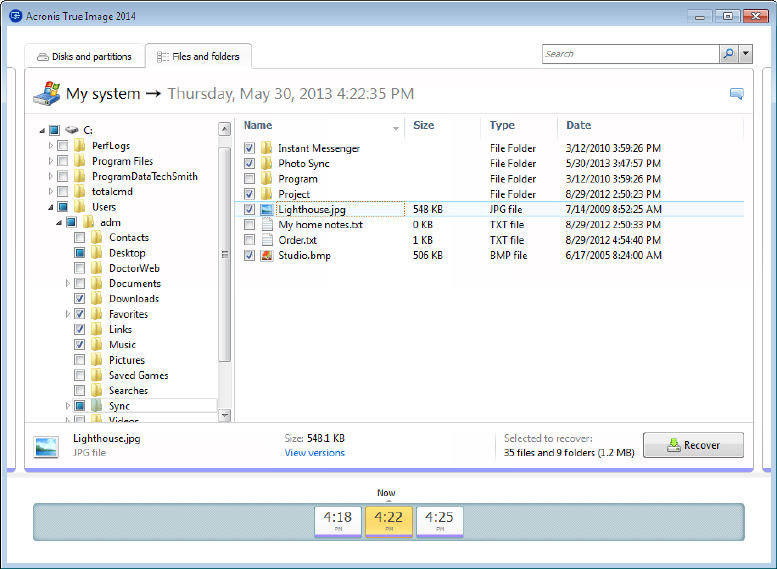
Acronis True Image 2019 20 NVme SSD indizieren und Backup wieder herstellenHow do I protect my computer? - Three simple steps to protect your computer with the best True Image feature. How do I back up my files? -. The True Image bootable recovery environment now also fully supports Acronis Cloud. If your system won't start, boot from the recovery disc. Acronis True Image ; Topics: manualzz, manuals, User`s guide, ; Collection: manuals_contributions; manuals; additional_collections ; Item Size.